Four lesser-known WiFi security threats and how to defend against them
It’s common knowledge that the best way to protect your home Wi-Fi network is by using a strong password. This will keep uninvited guests away and protect your network so eavesdroppers can’t intercept your communications. And we’ve known for more than a decade now that the old Wired Equivalent Privacy (WEP) is so insecure that cracking it is practically child’s play.
ALSO ON NETWORK WORLD: 9 tips for speeding up your business Wi-Fi
Once you’ve protected your network with Wi-Fi Protected Access 2 (WPA2), here are four other vulnerability scenarios you should guard against.
Change your default wireless settings
Some modem/router manufacturers and ISPs preconfigure their gear with Wi-Fi encryption using a default password. This is often printed on a label on the device itself or on its shrink wrap, so that your wireless network is protected from the instant you take it out of the box. Great idea, right? It’s not if that Wi-Fi password can be easily discovered.
One insecure default setting scheme used by various companies is putting a portion of the device’s MAC address and/or default SSID (network name) in the Wi-Fi password. For instance, my ARRIS gateway supplied by Time Warner Cable comes with the default SSID of TG1672G02 for its 2.4GHz network and TG1672G02-5G for its 5GHz network, both using a default password of TG1672G1E1F02. That looks fairly secure at first glance, since it’s at least a combination of letters and numbers, but its comprised partially of the gateway’s model number—TG1672G—and partially of its MAC address: D4:05:98:1E:1F:02.
 Eric Geier
Eric GeierHere’s the label on my ISP’s gateway, showing the insecure default Wi-Fi name and password.
With its default settings, my gateway’s SSID is clearly advertising the exact gateway model I have. A hacker could do some easy research to find known security holes. Secondly, the remaining portion of the default password is the last 6 digits of the gateway’s MAC address for 5GHz, marked as CMAC on my gateway’s label. This MAC address is also broadcast and can be picked up by anyone with a Wi-Fi analyzer as simple as a free Android or Windows app.
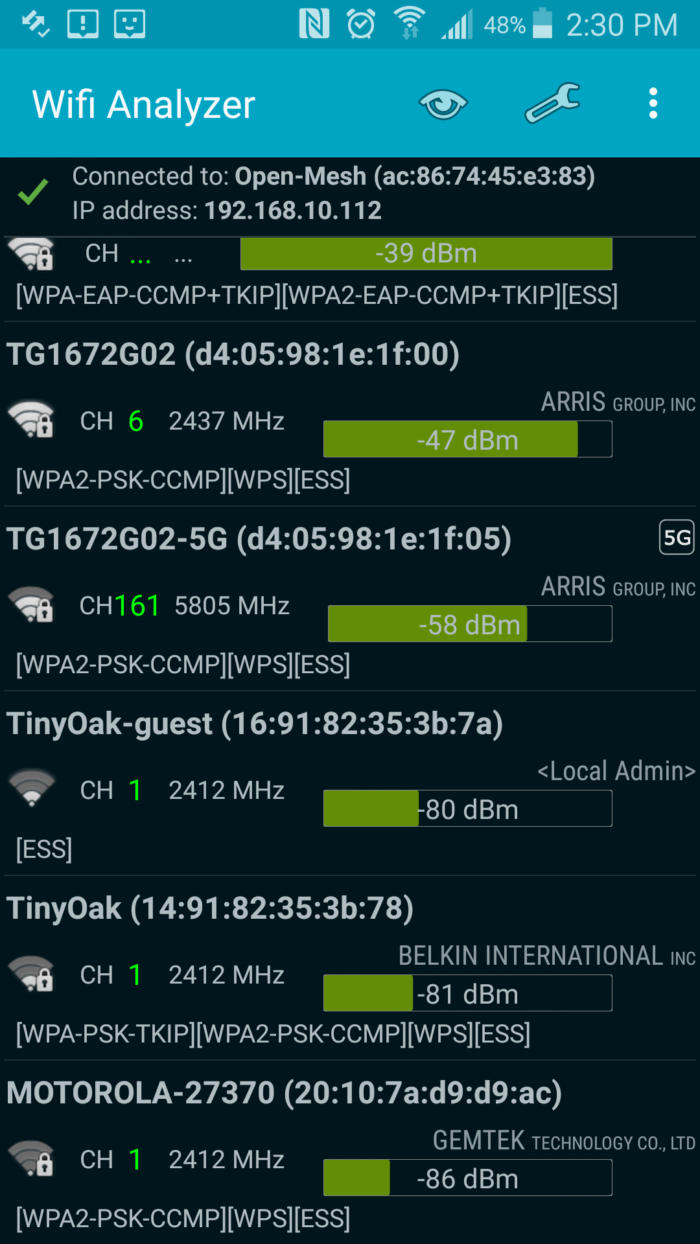 Eric Geier
Eric GeierHere’s the Wi-Fi Analyzer app, giving anyone within range who understands the password scheme all the details they need to connect to my Wi-Fi network.
Now that we know how the default Wi-Fi password is structured on these devices, we can likely connect to other people’s networks that have the same gateway model. A neighbor of mine actually has the same exact SSID as me, but it would likely be illegal for me to attempt to connect to it. So let’s assume for the sake of this argument that my neighbors didn’t change their default password and I could connect if I tried. Your neighbor (or a hacker driving by) might not be so nice, so take a few seconds to change your router’s and/or gateway’s default SSID and Wi-Fi password.
Lost or stolen Wi-Fi devices can be security threats
You can lock down your Wi-Fi with the most stringent security, but if you lose your smartphone, tablet, laptop, or any other device that you’ve connected to your Wi-Fi network, whoever recovers it will be in a position to access to every network you’ve connected to in the past, since those passwords will have been saved to that device by default. Depending on who recovers the device, where they found it, and how much info they can glean from it, they might even be able to figure out where those networks are physically located.
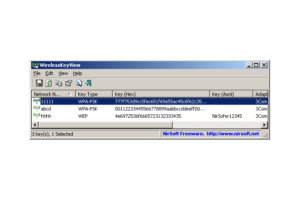 Eric Geier
Eric GeierHere’s an example of how thieves can use seemingly legit programs, such as Nirsoft’s WirelessKeyView, to reveal all the saved Wi-Fi passwords on your device.
If you lose a mobile device, see if you can remotely lock or even wipe it (you do back it up on a regular basis, right?) to prevent any unauthorized person from gaining access to the Wi-Fi passwords and any other data you have on it. Secondly, it’s a good idea to change the Wi-Fi password of all the networks you connected it to in the past. Some private networks might not be in your control, so you should notify the parties who are responsible for them—especially your employer.
If you’d been using the simple personal Wi-Fi security modes of WPA or WPA2—technically known as pre-shared key (PSK)—you’ll need to change the password on the gateway or router and then enter that new password on all your other network devices the next time they connect. That will be a moderate inconvenience for the typical home with just a handful of Wi-Fi devices. For a business with dozens of devices on its wireless network, it could be a major pain.
There is a means of mitigating the disruption of compromised passwords, but its complexity and infrastructure requirements put it outside the reach of the typical consumer. This version of WPA or WPA2 is typically called “enterprise mode,” and it works like this: Instead of everyone using the same Wi-Fi password to connect to the network, each user is assigned a unique user ID and password. Any user account that becomes compromised can be changed individually or revoked entirely without impacting anyone or anything else.
Keep in mind, there’s another mode of WPA and WPA2 Wi-Fi security, typically called enterprise mode, which delivers better protection against incidents like this. Instead of everyone using the same Wi-Fi password for the network, each user would receive their own username and password, which could always be individually changed or revoked if a device becomes lost or stolen.
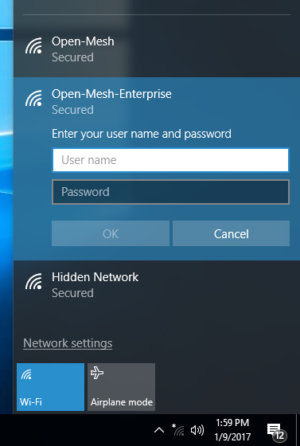 Eric Geier
Eric GeierHere’s an example of a login prompt users would see when connecting to networks with enterprise Wi-Fi security.
Enterprise mode’s barrier to entry is that 802.1X user authentication requires the presence on the network of a server running the RADIUS (Remote Authentication Dial-in User Service) protocol.
But if you’re running a small business or you’re super security conscious about protecting your home network, there are various cloud and hosted services that will run the server for you—IronWiFi and JumpCloud even offer free tiers, albeit with limited numbers of Wi-Fi access points and users and limited tech support. Don’t go down that path unless you know what you’re doing.
Your router’s WPS button can be a threat vector
The Wi-Fi Protected Setup (WPS) feature that many wireless routers come with is supposed to help make it easier to secure your Wi-Fi nerwork and connect devices with a quick push of a button or the entry of a PIN {personal identification number). Security holes in this protocol discovered many years ago, however, can allow hackers to gainn access to the network without their needing to crack the router’s Wi-Fi password. Since this vulnerability has been known for so long, I assume at least some vendors have patched this hole, but I’m equalsure there’s many vulnerable routers out there still.
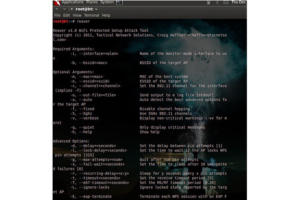 Eric Geier
Eric GeierReaver is a cracking tool that takes advantage of the weaknesses of WPS.
To be on the safe side, I recommend disabling the WPS feature on your gateway or router—if you can; unfortunately, some routers actually don’t allow this. If you don’t want to purchase a new router just because of this threat, you should check if there are any firmware updates for the router that could possibly patch this and other security holes.
Disabling SSID broadcasting can do more harm than good
One security tip that has circled the web since the beginning of Wi-Fi suggests disabling SSID (Service Set Identifier) broadcasting of your network, which is still possible on most wireless routers. Some say this will hide your network and keep people off, since they have to know the SSID in order to attempt a connection. There is a nugget of truth there, but it can do more harm than good.
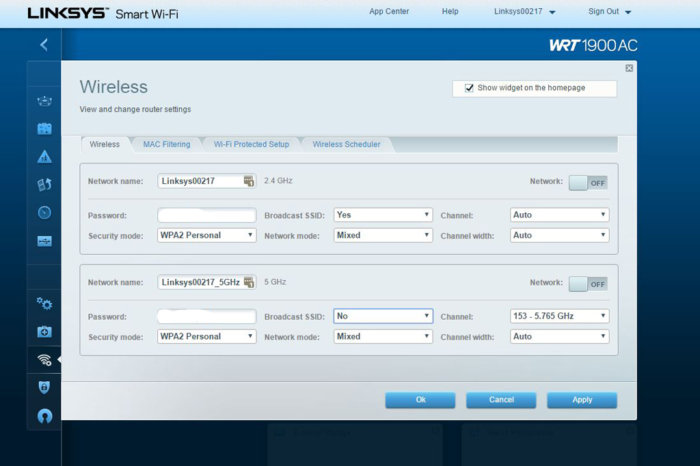 Michael Brown
Michael BrownYou can prevent your router from broadcasting your wireless network’s SSID, but that can have unforseen consequences.
When you configure your router to not broadcast your network’s SSID, you’re only removing the SSID from the beacons the Wi-Fi router sends to notify nearby Wi-Fi devices of the presence of that network. Those beacons are what populates the list of available networks on your laptops, smartphone, tablets, and other Wi-Fi devices. If the SSID isn’t included in the beacons, Windows devices these days will still indicate the presence of a network, it will just identify its name as “Hidden Network.” Other devices might show a blank name, or not show the network at all.
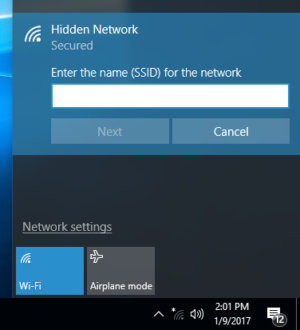 Eric Geier
Eric Geier“Hidden Networks” still appears in the Windows network list, so others will still know that there’s a network nearby.
Even if you disable SSID broadcasting, the SSID will nonetheless still be included—unencrypted—in some Wi-Fi traffic, where it can certainly be intercepted by eavesdroppers. The SSID is included in the association process, for example, so when a device connects or reconnects to the network, an eavesdropper could capture the SSID at that point. While Windows and most other devices natively won’t pick up on the SSID in this other traffic, it is captured by many third-party Wi-Fi analyzers, such as Kismet, CommView for WiFi, and Airmagnet.
Since the SSID can be so easily intercepted by eavesdroppers, I would never recommend disabling its broadcast in place of encryption. Disabling it after enabling WPA2 with a strong password might deter the most casual of hackers from attacking your network, but that can have a negative impact on a large network’s performance because it increases the amount of background traffic traveling over the network.
This story, “Four lesser-known Wi-Fi security threats and how to defend against them” was originally published byTechHive.
Join the Network World communities on Facebook and LinkedIn to comment on topics that are top of mind.







